Essential IT Policies Every Business Should Have in Place

Businesses face an ever-growing number of cybersecurity threats and operational challenges. Without well-defined IT policies, companies risk data breaches, compliance violations, and costly downtime. Whether your business is a small startup or an established enterprise, having the right IT policies in place is essential for security, efficiency, and regulatory compliance. 1. Acceptable Use Policy (AUP) […]
Your Employees Are Losing Devices. What’s the Fix?

Employees are often on the go, utilizing laptops, smartphones, and tablets to work remotely, access company data, and communicate with clients. But what happens when these devices are lost or misplaced? Unfortunately, this is not just an inconvenience—it can have severe consequences for your business’s security and data integrity. The Risks of Lost or Misplaced […]
Phillip Long, CEO of Business Information Solutions, Earns Certified Ethical Hacker Certification
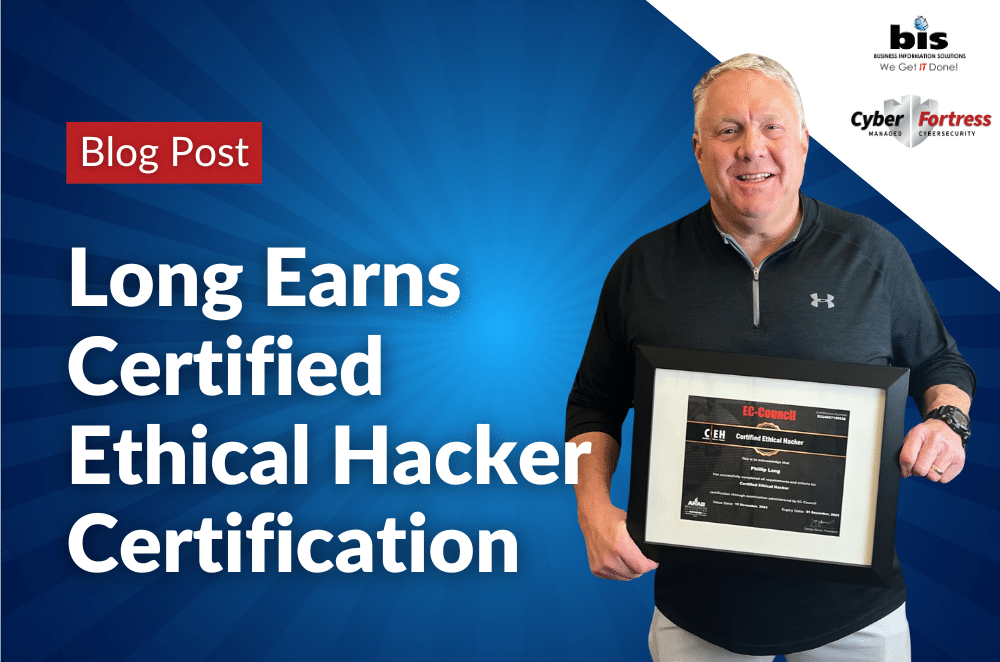
Robertsdale, AL – Business Information Solutions (BIS), a leading provider of IT support and cybersecurity services on the Gulf Coast, proudly announces that CEO Phillip Long, CISSP and CMMC-certified, has recently achieved the prestigious Certified Ethical Hacker (CEH) certification. This milestone underscores his dedication to staying ahead of evolving cyber threats and equipping businesses with […]
A Smart Tip for Saving on Computers and Software
As the holiday season approaches, business owners often turn their attention to year-end planning. For companies in Mobile, AL, Pensacola, FL, and throughout the Gulf Coast, this is the perfect time to leverage the Section 179 tax deduction. At Business Information Solutions (BIS), headquartered in Robertsdale, AL, we specialize in helping local businesses maximize their […]
How to Build a Cybersecurity Culture: Tips for Leaders and Managers

The world continues to become more and more digital making cybersecurity more critical than ever. With increasing cyber threats and data breaches, organizations must prioritize creating a robust cybersecurity culture. This culture not only protects sensitive information but also fosters an environment where employees are engaged and proactive about cybersecurity. As leaders and managers, your […]
The Cybersecurity Team: Who You Need to Have on Your Side

As we observe Cybersecurity Awareness Month, it’s essential for business owners to recognize the critical role that a dedicated cybersecurity team plays in protecting their organization. Threats are evolving rapidly, making it imperative to assemble a team equipped to safeguard your business against cyberattacks. But who should be on your cybersecurity team? Here’s a breakdown […]
How to Make NIST Compliance Easy for Architects and Engineers
As an architect, engineer, or contractor, you may be required to meet stringent NIST (National Institute of Standards and Technology) compliance standards. Achieving and maintaining these standards can be daunting, but understanding the process and having a clear path can simplify the journey significantly. Understanding NIST Compliance NIST compliance involves adhering to a set of […]
How AI Could Cause a Data Breach and Compromise Confidential Company Data
Artificial Intelligence (AI) has become an invaluable asset for businesses to enhance efficiency and enable innovation. However, alongside its benefits, AI also presents significant risks, particularly concerning data breaches and the compromise of confidential company data. Understanding these risks is crucial for businesses to safeguard their sensitive information. #1: Sensitive Company Data AI platforms like […]
Block the Breach – Why the Bad Guys Are Winning
The battle against cybercrime is more critical than ever. Cybercriminals continue to exploit vulnerabilities in systems and prey on unsuspecting businesses, leaving a trail of financial devastation in their wake. According to the Cost of Cybercrime Report, in 2022 alone, the global cost of cybercrime soared to a staggering $8.4 trillion. Shockingly, this number is […]
How to Secure Your Microsoft 365 App

With an increased remote workforce and on-the-go culture, businesses rely heavily on cloud-based platforms to streamline their operations and boost productivity. Microsoft 365 has emerged as a leading suite of applications providing a comprehensive solution for collaboration, communication and data management. However, with the increasing sophistication of cyber threats, it is imperative to prioritize the […]










